Let’s See What Are The Benefits Of Cyber Hygiene:
Before we discuss What Are The Benefits Of Cyber Hygiene, let’s see what the ‘Cyber Hygiene’ is.
What Is Cyber Hygiene?
We all know that to stay healthy we have to follow some health related rules and hygiene related rules have to be followed. Like eating healthy food, exercising, sleeping and waking up on time and following a regular routine etc.
Similarly, in today’s era, to run your organizations or business in a secure manner and keep it free from cyber attacks, you have to adopt some rules so that your data remains safe. The rules that have to be followed to keep your digital data safe are called ‘Cyber Hygiene’ in simple words.
Last year at the World Economic Forum’s annual meeting, a report was released highlighting the state of cybersecurity in critical infrastructure. At that time, nation-state attacks had doubled in just one year, high-profile supply chain attacks were on the rise, and the average data breach cost had reached nearly $4.5 million. Fast forward a year later, and much of it is still valid.
A survey has revealed that there is a strong relationship between cyber hygiene and growth in GDP of a country.
To assess global cyber health, cybersecurity scores were analyzed across 6.3 million organizations located in 189 countries located in 17 geographic regions around the world.
This data was combined with 2022 GDP per capita economic data published by the IMF. Regional cybersecurity hygiene scores and per capita GDP were calculated using respective country hygiene scores and per capita GDP data.
A summary of the data is as follows, including the number of countries and organizations contributing to each region’s cyber hygiene score-
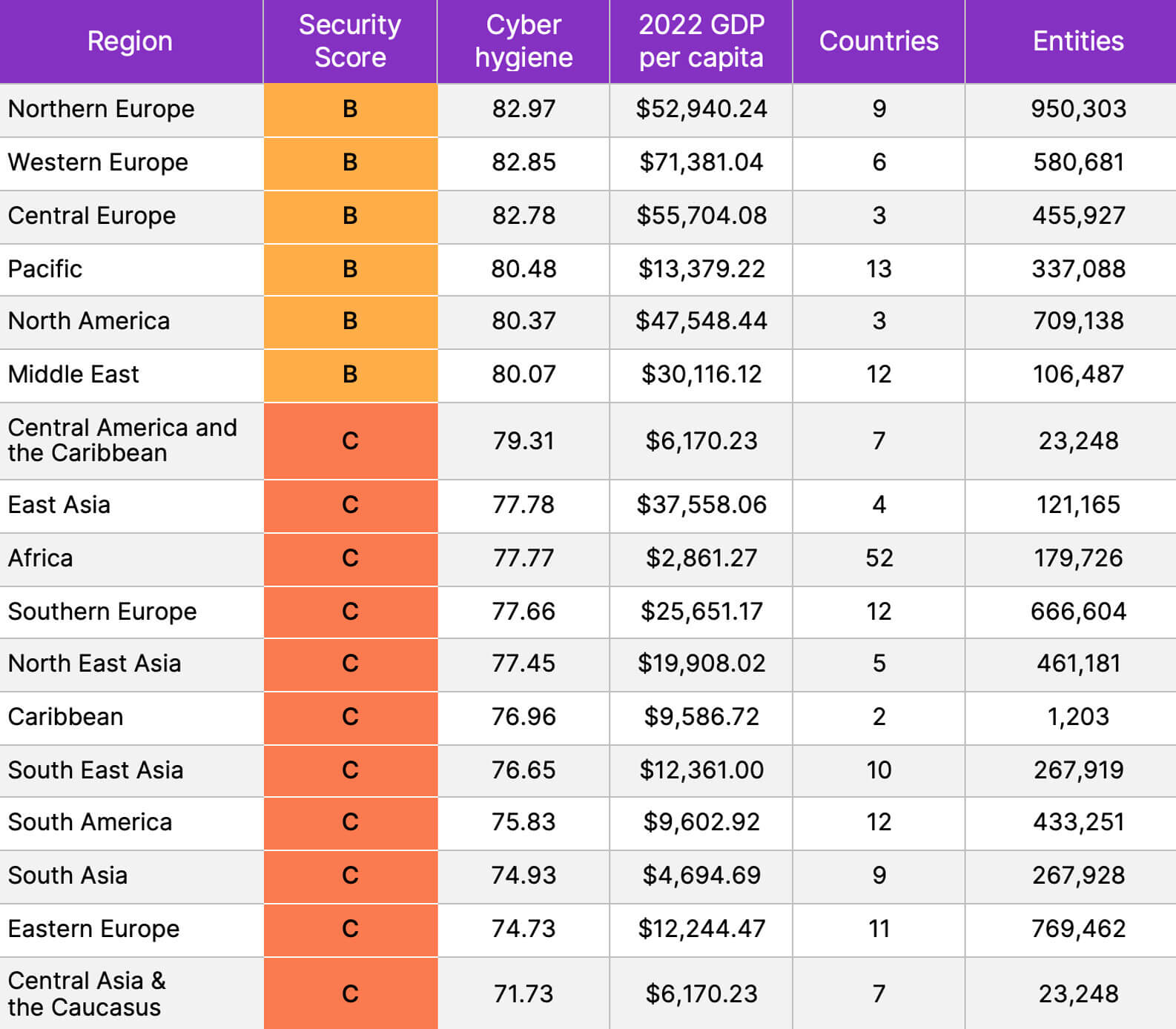
The risk of cyber threat in high GDP countries has been found to be less as compared to low GDP countries. Its main reason is that countries with high GDP are more able to invest in cyber security measures due to their strong economies.
The survey has also found that countries with high GDP are the main targets of cyber attackers.
You may also like:
- Digital Detox Advantages and Disadvantages: Best Practice 2024
- What Is Cyber Vandalism And How To Prevent It In 2024: Shocking Threat
- Cyborg Computer Combining AI and Human Brain Cells: Amazing Research 2024
Benefits Of Cyber Hygiene:
Strong cybersecurity hygiene is essential to protecting critical infrastructure like water, transportation, health care, energy, and financial services etc. If this is not done then there is a possibility of a very bad impact on the country’s economy and its financial status.
Just as it is important to adopt hygiene for physical health, in the same way in today’s digital technology era, it is also important for any organization to follow cyber hygiene rules to ensure cyber security in its business and to benefit from the protection of software.
Cyber attackers are adopting new methods of cyber attack by using modern technologies day by day. Every day new malware, viruses, trojans, worms and phishing etc. are being developed. To be safe from these, cyber hygiene will have to be adopted.

Why Cyber Hygiene Is Important?
Not following cyber hygiene can cause the following problems:
- Data Loss – If cyber hygiene is not followed then the security of the data can be at risk and it can be the cause of data loss. In absence of cyber hygiene, the security of data is at risk and it can lead to data loss. Without cyber hygiene, it can be very easy for cyber criminals to hack your precious data.
- Data may be missing or misplaced – It is quite possible that due to lack of cyber hygiene, you may not maintain your data properly and keep it in the wrong place and you will not be able to access it. It is possible that even if your data is not corrupted, you may still have trouble finding the data on time.
- Possible Breach of Security – In the era of technology like AI and machine learning, the nature of cyber crime has also changed and the methods of cyber attackers are more dangerous than before. To avoid this, it is important to follow cyber hygiene parameters.
- Compromised Software – Using older versions of software or not updating the software regularly can make the software vulnerable to cyber attacks and this can harm your business or organization.
- Consequences of using older/not updated versions of antivirus – If you use older or not updated antivirus then it can also make your system an easy target for cyber attackers.
Best Practices In Cyber Hygiene:
Cyber Hygiene is a regular routine or habits:
Cyber hygiene should be practiced regularly. You can create habits by setting automatic reminders for various tasks. These may include scanning for viruses using antivirus software, changing your password, keeping apps, software, and operating systems up to date, and cleaning your hard drive.
Use of effective tools:
- A network firewall should be used – This can prevent unauthorized users from accessing your websites, mail servers, and other sources of data that can be accessed from outside.
- Use of Data-wiping software – Whenever you introduce new software, add hardware, or modify system files, there may be a risk of losing personal data. Using data-wiping software allows you to clear data you don’t need and clear it from the hard drive.
- Using strong passwords and use of password manager – Using strong, complex passwords that you change regularly is an important aspect of cyber hygiene. Using a password manager can help you keep track of multiple passwords.
- Use of high quality and robust antivirus software – It can schedule and can automate device scans, detects and removes malicious software, and protects you against a variety of online threats and security breaches.
- You sometimes wonder how to safely dispose of old computers. If you’re selling or getting rid of your desktop, laptop, tablet or smartphone, it’s important to make sure that your personal or sensitive data isn’t sent along. Simply deleting your personal files or data is not enough. You must reformat and then clean your hard drive. A clean hard drive means you aren’t giving away your personal and precious information.
A Cyber Hygiene Checklist For You:
Password security and safety
- I try not to use the same password across multiple accounts.
- I frequently change the passwords I use.
- I try to use at least 12 characters in my passwords, but preferably more.
- I use a combination of capital and lowercase letters, symbols, and numbers in my passwords.
- My passwords steer clear of obvious things like sequential numbers (“1234”), or details about me that someone who knows me well could figure out, like my birthday or the name of a pet.
- I alter my Internet of Things (IoT) devices’ default passwords.
- I don’t share my passwords with anyone or write them down.
- To help create, save, and manage all of my passwords in one safe online account, I use a password manager.
Employing two-factor authentication
Using an app like Google Authenticator or Authy, I use multi-factor authentication (MFA) to secure all of my important accounts, including my banking apps, social media accounts, and email. I store MFA backup codes in my password manager.
Backing up data regularly
I back up important files offline, either to the cloud or an external hard drive, to ensure file security and prevent data loss.
Protecting Privacy
- I don’t publicly share personal details on social media, like my phone number, home address, credit card numbers, or private photos.
- I’ve checked to make sure my social media privacy settings are at a level that I’m comfortable with.
- I steer clear of social media surveys, games, and quizzes that request sensitive personal information.
- I exercise caution when accepting permissions from all the apps I use.
- I use a password or PIN to lock down my computer and phone.
- I take precautions not to reveal personal information when using public Wi-Fi.
- I am aware that utilizing a Virtual Private Network, or VPN, enhances my privacy, particularly when utilizing public Wi-Fi.
- I always make sure that any online purchases I make are made on secure websites, identified by a padlock icon to the left of the address bar and a URL that begins with https:// rather than http://.
- To keep my loved ones safe online as well, I also educate them about privacy issues.
Keeping firmware, software, and apps updated
- I constantly update my operating systems, firmware, web browsers, and apps to ensure I’m running the newest versions, which have fixed or removed any potential security flaws.
- I have installed features to guarantee automatic software updates wherever I can.
- I delete apps I’ve stopped using
- I only download apps from reliable, authorized websites.
Protecting routers
- My home Wi-Fi default name has been changed.
- I keep the firmware on my router updated, and I have changed the username and password.
- I’ve turned off Wi-Fi Protected Setup, Universal Plug and Play, and remote access.
- I have ensured that my router supports WPA2 or WPA3 encryption and have set up a separate network for visitors to use.
- I don’t click on dubious or questionable links. I’m not sure why, but I don’t open emails that seem fishy.
- I steer clear of opening dubious attachments from texts or emails.
- I don’t click on advertisements that offer discounts, freebies, or prizes, so I’m not expecting anything.
Implementing firewalls on networks
- I utilize a firewall to stop malicious software from connecting to my network or computer over the internet.
- I make sure my firewall is set up properly.
Device encryption
I encrypt media and other devices that hold private information, such as backup tapes, cloud storage, laptops, tablets, and smartphones.
Deleting data from hard drives
I always make sure to completely wipe the hard drive of a computer, tablet, or smartphone before selling or discarding it to keep any private data from being accessed by third parties.
Ensuring High quality antivirus support
- I make use of premium antivirus software, which finds and gets rid of malware and other computer viruses.
- I make sure my antivirus program is up to date.
Conclusion:
In this article we saw how important it is to adopt cyber hygiene parameters to avoid the constantly evolving methods of cyber attacks by cyber attackers. Furthermore, we also discussed the best practices of cyber hygiene and by implementing this, you and your organization can remain safe from cyber threats to a great extent.
That’s all for now my friend! I hope this article will be valuable for you. You can reach me through the emails given below. I will love your valuable comments and feedback.
Yours
Abhijit Ranjan
2 thoughts on “What Are The Benefits Of Cyber Hygiene? Best Practices In 2024”