With the advancement of the digital world, the chances of theft of your personal data by hackers are increasing. One of these is “Juice Jacking”. In today’s article we will see what is a Juice Jacking, how to prevent this attack and which device may protect your phone from juice jacking.

What is a Juice Jacking?
In today’s world almost everyone has a smartphone. Whenever people stay out of the house for a long time, go somewhere or travel, they often find themselves in a situation where the battery of their mobile phone gets discharged. In such a situation, people use the charging station available at any public place to charge their mobile phones. The game of hackers starts here. They can steal personal data stored in your mobile phones by using these public charging stations. This is called Juice Jacking.
How Juice Jacking Works?
The possibility of Juice Jacking attack occurs in public places charging stations which provide USB charging facility. These include mainly railway stations, airports, shopping malls, bus stops and many other places. Even a public Wi-Fi facility is not safe. Hackers can put malware in your mobile phones through these USB charging stations using USB connection which can give access to hackers to steal your personal information, your bank accounts details etc. which may put you in problem. Since data is transferred over the same port that is used to charge a device, juice jacking vulnerabilities are effective.
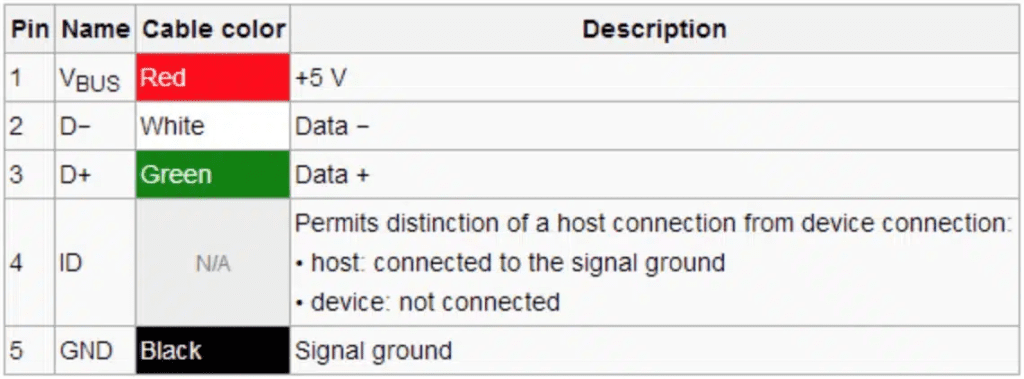
There are five pins in a USB Connector. However, only two of the five pins are required for data transfer, and only one is required to charge a connected device. When the mobile device is plugged into the charging station, this architecture allows the user to transfer files between the mobile device and the computer. In most cases, juice jacking assaults exploit USB ports and phone charging cords as their primary tools. Other uncommon gadgets could include portable battery power banks and USB ports found in video arcade systems.

What are the Types of Juice Jacking?
Juice jacking attacks come in a variety of forms, which are described here.
- Juice jacking attack for data theft: One of the common objectives of juice jacking attacks is exfiltrating the personal information of the users. Usually, the actual data theft is completely automated and occurs very rapidly. Furthermore, because of how close we are to our phones these days, credit cards, bank accounts, emails, medical records, and other important information could be stolen.
- Installation of Malware or Virus by Juice Jacking: When malware or virus is installed in your phone, it can cause a lot of harm to you. Your device may be compromised, you may be monitored by spying, your device may be locked, your device may become slow, your important information and bank details may also be stolen, random network connection may also occur, etc.
- Juice Jacking Attack Multi-Device: Effect of Multi-Device Juice Jacking attack is similar to what attackers do through malware or virus attacks. In this, malware is designed in such a way that it not only causes harm to the device which is infected first, but it also infects all the devices and USB charging ports which come in contact with the infected device.
- Juice Jacking Attack by Disabling the Device: The disabling juice jacking attack just disables your mobile device. The attacker will load malware onto the phone after it is linked to the compromised charging port, so making it inoperable for the authorized user while keeping complete control over the device. After a juice jacking attack is disabled, the same risks as previously apply, plus there’s the possibility that it could be utilized in a DDoS attack.
You may also like:
What Devices can be Attacked by Juice Jacking:
The majority of juice jacking incidents occur on mobile devices. However, this does not imply that mobile phones are more susceptible than other types of equipment to juice jacking assaults. The reason for this is because they are the most often used mobile devices, making them the ones that require a quick charge when on the road.
However, any electrical device that uses USB charging is susceptible. This includes tablets and Smartphone, as well as fitness trackers, smartwatches, and laptops (if they have USB charging capabilities).
How To Prevent Juice Jacking Attacks?
Some tips have been shared by Federal Communications Commission (FCC) of US to avoid Juice Jacking attacks. These are as follows:
- Use of AC power outlets for charging your device.
- Carry an external battery.
- Always keep charging only cable.
- Whenever you plug your device into USB charging station, always select “Charge Only” prompt in place of other prompts appear on your device’s screen.
In addition to the above tips, you should also keep the following things in your mind which will help you in preventing Juice Jacking attacks:
- Try to avoid public charging stations for charging your mobile phones or other devices. It is better to switch off your mobile or gadgets rather than get your data stolen.
- Always use your electrical (AC) charger in place of USB charging cable while in public places.
- Don’t charge your mobile phones or other USB gadgets from un-trusted devices or others’ laptops or computers.
- Always keep a good quality Power Bank with you while you are travelling or outdoor for a long time.
- Keep the software of your mobile phones or devices updated and use good quality anti-virus.
- Try to avoid public wi-fi connectivity.
- Keep automatic connection of your device closed.
- Another good idea is to keep your device switch off while charging in public charging stations. It will help you avoiding such situations.

Which Device may Protect Your Phone from Juice Jacking?
As said earlier, always try to avoid public charging stations. However, in case of extreme necessity, some devices may also help you in protecting your phone from juice jacking attacks. These are:
- Only charging USB cables: Use “Only Charging” USB cables.
- USB Condoms: This is the device which sits between USB Charging Ports of public charging station and your device which can protect you from such type of incidents.
- Juice jack defender: It is a special device which can defend you from Juice Jacking attacks. It can block malware or virus and can charge your mobile devices i.e., phone, tablets, laptops etc. without any data sharing.
Juice Jacking Attacks in India:
Indian leading bank State Bank of India (SBI) has appealed to the people through its official Twitter handle not to plug your mobile devices at charging stations. Recently, the CEO of a company in Hyderabad, India suffered a loss of Rs. 16 lakh due to a juice jacking attack. This type of incident is becoming more common in India.
History of Juice Jacking Attack:
In August 2011, during the DEF CON hacker conference, juice jacking first appeared. Free mobile device charging stations were provided to conference attendees. A notification alerted customers to the possibility that the devices had malicious programming, so they should not believe promises of free charging that seem too good to be true just because it’s convenient.
Apple and Android upgraded their Smartphone in reaction to juice jacking, giving customers the option to select whether to trust the charging port, power bank, or other charging procedure and alerting them every time they charge. Users’ devices only allow data transfer when they select the un-trusted device option; they cannot be used for data transfer.

Conclusion:
Thus we have seen in this article how we can avoid malware attacks like Juice Jacking by using the above precautions and keep our valuable data safe.
That’s all for now my friends. I hope, this article will be valuable for you. You can reach me on the email addresses given below. I will always love your valuable feedbacks and suggestions.
Yours
Abhijit Ranjan